Former Conti Members and Fin7 APT Unite to Unleash New Domino Backdoor
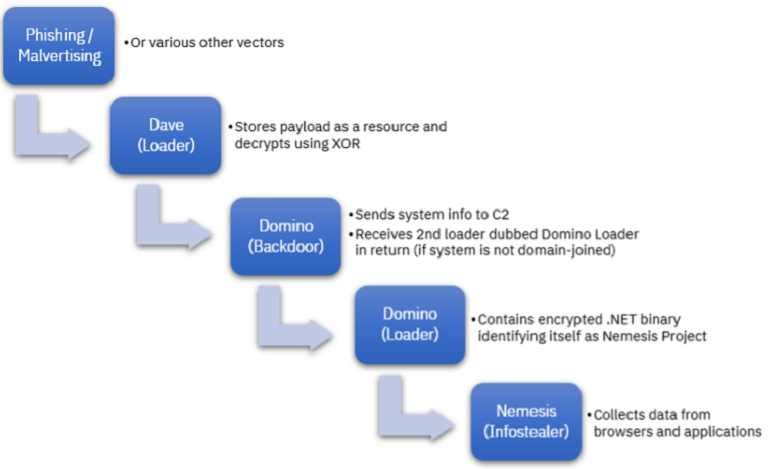
The discovery of a new malware campaign by IBM Security X-Force researchers in February 2023 highlights the complex and interconnected nature of modern cybercrime. The campaign, linked to the ITG23 group and the FIN7 Advanced Persistent Threat (APT) group, utilized a new backdoor called “Domino,” which was designed to deploy either the Project Nemesis info-stealer or Cobalt Strike.
This use of multiple malware types in a single campaign underscores the need for organizations to adopt a comprehensive and proactive approach to cybersecurity. The Domino backdoor and loader share coding styles and configuration structures and bot ID formats with the Lizar malware, and X-Force researchers found evidence connecting the Domino backdoor to FIN7’s Carbanak backdoor. The Domino backdoor has been active in the wild since at least October 2022, and it collects and sends basic system information to an actor-controlled command-and-control (C2) server.
The use of malware in this campaign highlights the intricate relationship between cybercriminal groups and their members, making it a challenging task for organizations and security teams to track threat actors. To identify and understand the scope and extent of such attacks, organizations need a robust Threat Intelligence Platform (TIP), which can enrich, and correlate Indicators of Compromise (IoCs) associated with a threat and take necessary actions to stay safe.
Cybercriminals have become increasingly sophisticated in their attacks in recent years, relying on a variety of tactics, techniques, and procedures (TTPs) to achieve their goals. These TTPs may include social engineering, spear-phishing, and the use of malware. In some cases, cybercriminals may also utilize multiple malware types in a single campaign to increase their chances of success, as seen in the Domino campaign.
To defend against these attacks, organizations must adopt a comprehensive and proactive approach to cybersecurity. This approach includes implementing strong security measures, such as multi-factor authentication and intrusion detection systems, and developing robust incident response plans. Organizations must also stay up to date with the latest threat intelligence and adopt a continuous monitoring strategy to detect and respond to threats in real-time.
One of the significant challenges organizations face in defending against cyber-attacks is the ever-changing nature of the threat landscape. Cybercriminals are constantly evolving their tactics and techniques, making it difficult for organizations to keep up. For this reason, organizations must prioritize their cybersecurity efforts and allocate resources accordingly. This may involve investing in advanced technologies, such as artificial intelligence and machine learning, to help detect and respond to threats.
See more: Foreign Diplomatic Entities targeted by Russia Linked Hackers
Another critical aspect of a comprehensive cybersecurity approach is employee education and training. Many cyber-attacks, including phishing and social engineering attacks, rely on human error. By educating employees on how to recognize and avoid these types of attacks, organizations can significantly reduce their risk of falling victim to a cyber-attack.
See more: China’s APT41 Group Exploits Open-Source Red Teaming Tool GC2
The Domino malware campaign serves as a reminder of the complex and interconnected nature of modern cybercrime. Organizations must adopt a comprehensive and proactive approach to cybersecurity to stay ahead of cybercriminals. By implementing strong security measures, developing robust incident response plans, and staying up to date with the latest threat intelligence, organizations can protect their critical assets and mitigate the risk of a cyber-attack. Employee education and training are also critical components of a comprehensive cybersecurity approach, as human error remains a significant factor in many cyber-attacks.
Author: Manjushree Gavitre
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn