Iranian Hackers Use a Powerless Backdoor to Execute Attacks
Iranian state-sponsored hackers have been accused in recent years of waging cyberattacks against a variety of targets including government organizations, enterprises and individuals. One of the technologies they employ is a backdoor called “PowerLess” that allows them to infiltrate and control computer systems.
PowerLess is a backdoor that allows attackers to get remote access to a compromised system. It was found in 2017 by Palo Alto Networks researchers, who identified it as being used by the Iranian hacker organisation APT33. It has now been spotted being utilised by other Iranian hacking groups.
PowerLess is often deployed to a target system via a spear-phishing campaign or a phishing email. Once installed on a system, it runs by connecting to an attacker-controlled command and control server. This server can send commands to the backdoor, allowing the attackers to control and access the hacked system remotely.
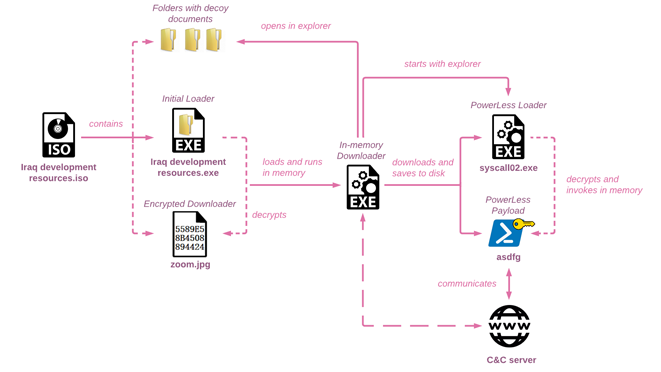
PowerLess’s usage of steganography is one of its most remarkable aspects. This is a method of concealing information within other data. The backdoor in PowerLess is concealed within a picture file, which is subsequently forwarded to the recipient as an email attachment. Following that, the backdoor is extracted from the image file and installed on the target system.
See more: FIN7 Hackers Caught Exploiting Veeam Vulnerability
Iranian hackers’ exploitation of PowerLess has serious consequences for cybersecurity. When a system is compromised, attackers can use it to steal important data, disrupt operations, or launch additional assaults against other targets. This has major implications for both persons and organisations.
Furthermore, the use of steganography to conceal the backdoor within an image file makes detection by regular antivirus software more challenging. As a result, systems may be compromised for longer periods of time before the assault is recognised and resolved.
See more: Google disrupts the CryptBot info-stealing malware operation
Iranian hackers use PowerLess as a backdoor to infiltrate and manipulate infected systems. It is difficult to detect due to its use of steganography, and its presence on a system can have major repercussions for cybersecurity. As a result, it is critical for individuals and organisations to be aware of the threat posed by PowerLess and to take precautions against such attacks. Implementing effective cybersecurity measures include utilising up-to-date antivirus software and training users on how to spot and avoid phishing emails.
Author: Jasmine Sahoo
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn






