Lockbit ransomware infects over 12K companies
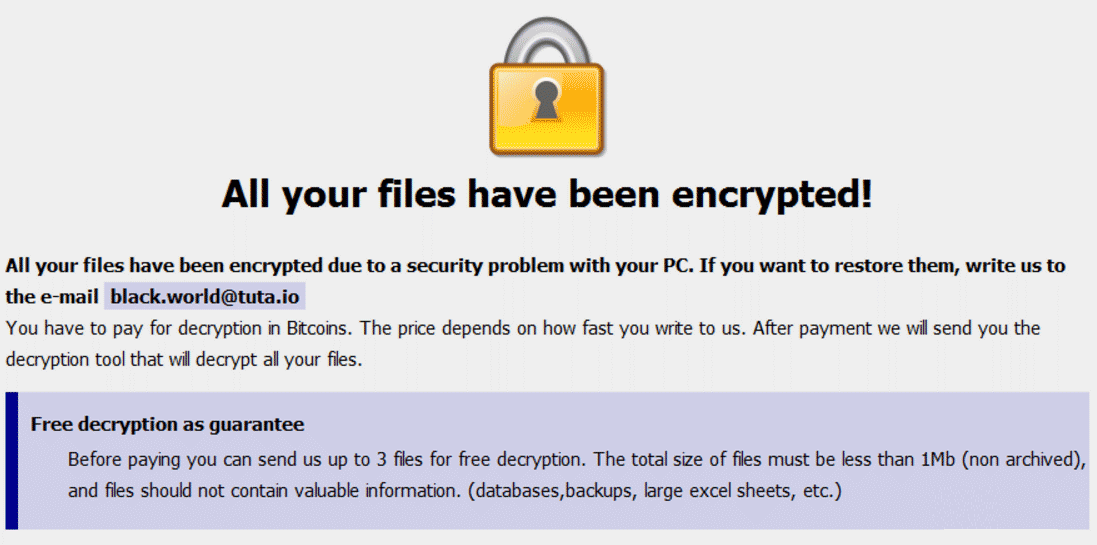
Imagine getting the below message alert in your office laptop screen.
‘Oops your files have been encrypted‘ or ‘Ransomware Alert‘ message flashes on the screen.
The moment you get this message, one starts thinking of “backup” or Do I need to pay ransom to get my file back and other thoughts.
LockBit is a ransomware which is formerly known as “ABCD” ransomware. since then it has grown into a unique threat within the scope of these extortion tools. LockBit is a subclass of ransomware known as a ‘crypto virus’ due to forming its ransom requests around financial payment in exchange for decrypting the data. It focuses mostly on corporate and government organizations rather than individuals.
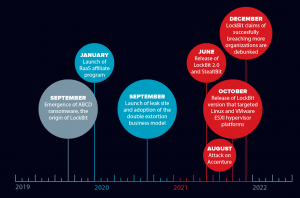
LockBit uses a ransomware-as-a-service (RaaS) model and consistently conceived new ways to stay ahead of its competitors.
It is believed that Lockbit ransomware has infected more than 12000 companies including Accenture and Merseyrail and collected ransom in billions from these companies.
LockBit ransomware is considered to be part of the “LockerGoga & MegaCortex” malware family which means it shares behavior with these established forms of targeted ransomware. It is also understood that these spread as in the following ways:
- Self-spreading within an organization rather than requiring manual direction.
- Targeted rather than spread in a scattershot fashion like spam malware.
- Using similar tools to spread, like Windows Powershell and Server Message Block (SMB).
Stages of LockBit attacks:
LockBit ransomware normally attacks roughly in three stages:
- Exploit
- Infiltrate
- Deploy
How to protect yourself against LockBit ransomware?
- Always implement strong passwords.
- Activate 2FA or multi-factor authentication.
- Set RBAC for the account which are to be used.
- AD and account reconciliation on timely basis.
- Ensure system configuration are following all security procedures.
- Always have system-wide backups and clean local machine images prepared.
- Ensure to have a comprehensive enterprise cyber security solution in place.
See more: https://www.latesthackingupdates.com/mobile-hotspot-tethering-a-big-no-read-to-know-why/
See More: https://www.latesthackingupdates.com/infamous-ransomware-gang-revil/
Follow us on facebook for more upates