Hackers Exploit Kubernetes RBAC to Deploy Backdoor
Kubernetes has become a popular container orchestration platform in recent years, with many organisations using it to manage and deploy containerized applications. However, as its popularity grows Kubernetes has become a target for fraudsters looking for methods to exploit its vulnerabilities.
The Kubernetes Role-Based Access Control (RBAC) system, which is used to control access to resources within a Kubernetes cluster, is one such vulnerability. RBAC is a valuable tool for managing access to Kubernetes resources, but if it is misconfigured, attackers can use it to gain unauthorized access to the cluster.
Recently, a group of attackers used RBAC to deploy a backdoor in a Kubernetes cluster, allowing them to maintain persistent access to the system. This attack is known as the Inaugural attack and has been observed in the wild. The attacker first gains access to the Kubernetes cluster, either through a misconfigured Kubernetes API server or a compromised Kubernetes node. Once within the cluster, the attacker employs RBAC to create a new role with full access to all resources.
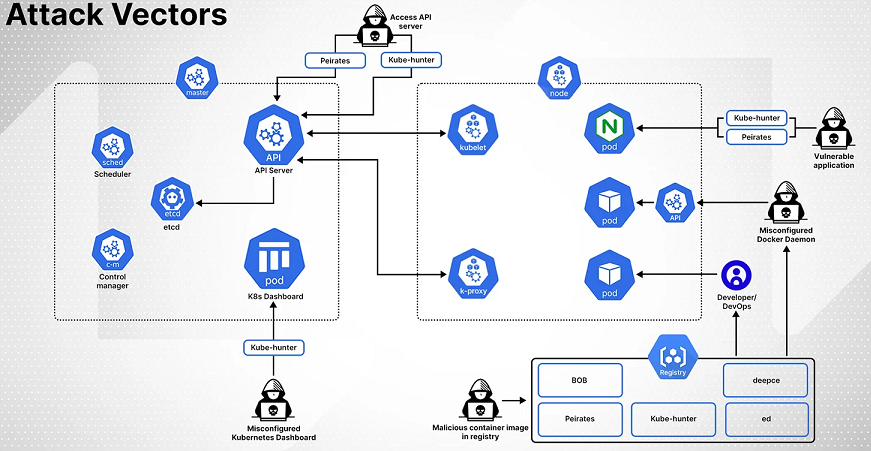
The attacker then establishes a new service account and associates it with the previously generated role. The attacker can now authenticate and communicate with the Kubernetes API server using the new service account and the credentials granted by the role.
See more: 8220 Cryptojackers Use Log4Shell to mint Coins
Using this access, the attacker can then deploy a backdoor in the cluster such as a container with a reverse shell or a pod with a malicious script. This backdoor allows the attacker to maintain persistent access to the system and potentially exfiltrate sensitive data or launch further attacks on the infrastructure. To avoid this type of attack, ensure that RBAC is properly configured in your Kubernetes cluster. Access to the Kubernetes API server is restricted, as are the permissions granted to service accounts and roles.
It is also recommended to regularly audit and monitor your Kubernetes cluster for any signs of unauthorized access or suspicious activity. This can include reviewing logs and monitoring network traffic to and from the cluster.
See more: Papercut Vulnerability being exploited by hackers! Know how
The Inaugural assault emphasizes the need of adequately protecting your Kubernetes cluster and using RBAC best practices. You may lessen the chance of falling victim to these types of assaults and protect your sensitive data from thieves by taking proactive actions to secure your infrastructure.
Author: Jasmine Sahoo
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn






