A new blind eagle attack chain has been discovered
Cyberattacks have increased in recent years, and threat actors are always devising new techniques to avoid detection and compromise systems. The Blind Eagle assault chain is one such recently found attack chain.
The Blind Eagle attack chain is a complex assault chain used by threat actors to acquire unauthorized network access. The assault chain is made up of several phases, each designed to avoid detection and make it difficult to track down the attacker.
The Blind Eagle attack chain begins with the attacker sending the recipient a phishing email. The phishing email typically includes a malicious attachment or a link to a website where malware is downloaded into the victim’s machine. The attacker takes control of the victim’s machine after installing the malware and can use it to move laterally within the target’s network.
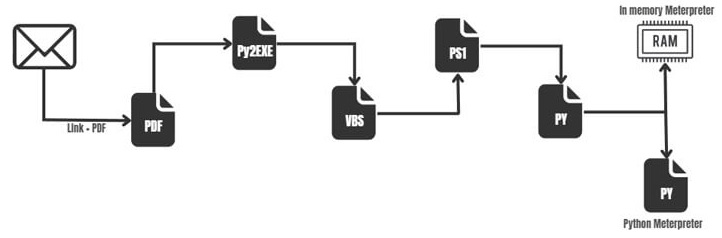
The following phases comprise the Blind Eagle assault chain:
Phishing occurs when an attacker sends a phishing email to a victim that contains a malicious attachment or a link to a website that downloads malware onto the victim’s machine.
The virus is placed on the victim’s computer, granting the attacker control of the machine.
Communication for command and control (C2): The attacker establishes contact with a remote server, allowing them to transmit commands to the compromised machine.
Lateral movement: The attacker moves laterally into the target’s network in search of valuable data and systems to compromise. The attacker acquires administrative access to the target’s network, allowing them to access sensitive data and systems.
Data exfiltration: The attacker completes the attack chain by transferring the stolen data to a remote server.
How to defend against the Blind Eagle attack chain?
Protecting oneself from the Blind Eagle attack chain necessitates a multi-layered security strategy. Here are some precautions you may take to safeguard yourself:
Utilise email filters: Email filters can assist detect and prevent phishing emails from reaching your inbox.
Maintain software updates: Keeping your software up to date with the most recent security updates can assist to prevent malware from exploiting system vulnerabilities.
Use anti-malware software: Malware detection and removal software can assist you in detecting and removing malware from your machine.
Limit administrative privileges: Restricting administrative privileges to those who require them can aid in the prevention of privilege escalation attacks.
See more: A new credential-stealer Zaraza bot targets 38 browsers
Implement network segmentation: By limiting lateral movement inside your network, you may make it more difficult for attackers to penetrate your systems.
Monitoring your network for unexpected behaviour can assist in detecting assaults before they do substantial damage.
See more: Lockbit adds Fullerton India Credit Company to victim list
The Blind Eagle attack chain is a complex assault chain used by threat actors to acquire unauthorised network access. To defend against this attack chain, use a multi-layered security approach that includes email filters, anti-malware software, restricting administrator access, adopting network segmentation, and monitoring your network for odd activities. By taking these precautions, you may help to protect yourself from this and other sophisticated cyberattacks.
Author: Priyanka Priyadarshini Dwibedy
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn






