The Tor browser installation contains malware that steals cryptocurrency
Russian and Eastern European users have been the target of clipper malware since September 2022, which infects the TOR anonymity browser, installs, and steals cryptocurrency.
Clipboard injectors “may be silent for years, displaying no network activity or any other signs of presence until the disastrous day when they swap a crypto wallet address,” claims Vitaly Kamluk, director of global research and analysis team (GReAT) for APAC at Kaspersky.
The fact that the malicious features of clipboard malware are not activated until the copied data satisfies particular requirements makes it more evasive.
By obscuring the user’s IP address and encrypting their traffic, the Tor Browser is a specialized web browser that enables anonymous web browsing.
Tor can also be used to access unique onion domains, commonly referred to as the “black web,” which are inaccessible via conventional browsers or ordinary search engines and are only accessible through Tor.
Cryptocurrency owners can use the Tor browser to access illegal dark web marketplace services that accept cryptocurrency payments or to increase their privacy and anonymity when trading with cryptocurrencies.
Trojanized Tor installations are frequently pushed to users in nations where Tor is forbidden or marketed as “security-enhanced” variants of the official vendor, the Tor Project, making it more difficult to acquire the original version.
According to Kaspersky, these installers include a regular, albeit frequently out-of-date, Tor browser in addition to an additional application that is concealed inside a password-protected RAR package that is configured to self-extract on the user’s computer.
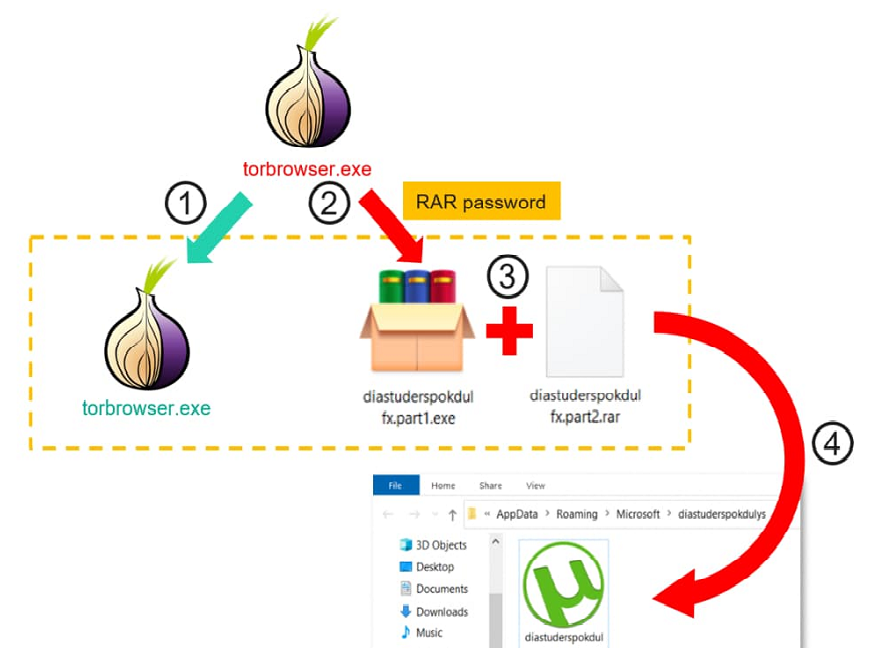
Users can select their preferred language from language packs in the installers, which are also localized with names like “torbrowser ru.exe.”
It’s not obvious how the installers are delivered, but evidence suggests that it may be through torrent downloads or some other unidentified third-party source given that Russia has recently imposed blockades on the Tor Project website.
Regardless of the method, the installer simultaneously launches the standard executable and the clipper payload, which is designed to monitor the contents of the clipboard.
According to Kamluk, if the contents of the clipboard contain text, a set of embedded regular expressions are used to scan them. If it does, a random address is chosen from a list that is hardcoded in its place.
Each sample contains thousands of potential replacement addresses, which are randomly chosen. Also, a feature likely implemented during testing allows the infection to be turned off using a unique hotkey combination (Ctrl+Alt+F10).
Around 16,000 detections were made, according to the Russian cybersecurity company, with the bulk occurring in Russia and Ukraine, followed by the United States, Germany, Uzbekistan, Belarus, China, the Netherlands, the United Kingdom, and France. The threat has been identified in 52 different nations worldwide.
The theft of Bitcoin, Litecoin, Ether, and Dogecoin is thought to have brought the scheme’s perpetrators over $400,000 in illegal gains. Due to the service’s secrecy characteristics, it is unknown how much Monero money was stolen.
See more: Pakistan linked cyberattacks and the SideCopy Connection
Due to the likelihood that the threat actors may be using additional software installers and as-yet-unknown distribution techniques to target naïve consumers, it is speculated that the campaign may have a wider scope.
It is usually advised to only download software from reputable and trusted sources to protect against such dangers.
Due to their length and complexity, bitcoin addresses are frequently copied to the clipboard before being pasted into a different programme or website.
Using regular expressions, the malware scans the clipboard for recognizable crypto wallet addresses, and when one is found, it replaces it with a related cryptocurrency address controlled by the threat actors.
The threat actor’s address will be pasted instead of the user’s cryptocurrency address when the user copies and pastes, giving the attackers access to the sent transaction.
According to Kaspersky, the threat actor chooses thousands of addresses at random from a hardcoded list for each malware copy. Due to this, tracking, reporting, and banning hard.
See more: India blocks 500 apps over spoofing concerns
The cybersecurity firm discovered that they had stolen about $400,000, excluding Monero, which cannot be tracked, after unpacking hundreds of malware samples they had amassed to extract the replacement addresses.
Installing software from unreliable or unofficial sources, in this example the Tor Project website, puts you at risk from clipboard hijackers. Copy and paste the following address into Notepad to see if you have been infected by a clipper: bc1heymalwarehowaboutyoureplacethisaddress.If it is altered, your system is vulnerable.
Author: Priyanka Sonawane
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn






