High severity flaw allowed hackers repojacking GitHub Repository
Recently a vulnerability was discovered in Github and Github acknowledged the exposed vulnerability as repojacking where hackers were able to control the repository.
According to Checkmarx a security company, the vulnerability left multiple packages susceptible to being hijacked to serve malicious code to millions of users and other applications.
See more: Airline Argentina passenger data has been compromised
It is reported that on June 13, researchers from Checkmarx reported this vulnerability. This vulnerability was acknowledged by Github as having “high” severity. The researchers were in return paid a hefty bug bounty amount. GitHub has not responded to the issue however Checkmarx has confirmed that the bug was worked upon.
This vulnerability, if not addressed, could have infected millions of users and the information could have benefitted crypto miners and provided other opportunities to the threat actors. Moreover, if the threat actors could have taken the control of the repository, they could have changed the source code by adding their own codes.
See more: Black Reward gang breached Iranian Nuclear power plant
Aviad Gershon quoted:
This vulnerability hits one of the links in the supply chain. Once this supply chain has been compromised, one can expect this incident as big as Solarwind and other bigger incidents.
A similar vulnerability was discovered in May wherein the hackers infected two popular PHP packages. It was later found that one of them had been downloaded more than 2 million times during the breach.
See more: Daixin team- A ransomware group targeting healthcare industries
The entire issue revolves around the “Popular repository namespace retirement” GitHub feature. Most of GitHub users change their user names, leaving namespaces including their old user names exposed. As per security researcher, Aviad Greshon, attempts to exploit the namespace retirement attribute remain a striking attack point for supply chain hackers.
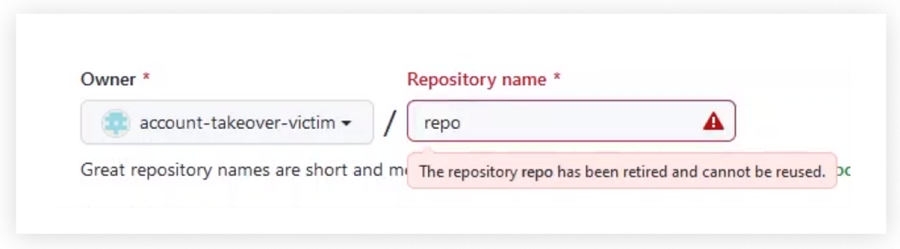
Researchers stated that any adversary could have exploited this vulnerability using the “Repojacking” technique – which allows an attacker to attempt to hijack a legitimate, popular namespace on GitHub. For example, once a user changes his/her username, the old username will be available for anyone to claim. An adversary can open a repository under the matching name, and claim the namespace.
To remediate this issue, GitHub introduced a feature where any repository that meets certain criteria is considered as “retired” and cannot be used by any other user.
Follow on Facebook: Latest Hacking Updates






