IBM Aspera Faspex Exploited by the IceFire Ransomware
Threat actors which are linked to the IceFire ransomware are now aggressively utilizing a deserialization vulnerability in IBM’s Aspera Faspex file-sharing software on Linux servers all over the globe using a new specialized encryptor.
A formerly recognized IceFire ransomware based on Windows is now targeting Linux business networks, which is now a larger part of IceFire’s mission. IceFire appears to be utilizing a known vulnerability that is still unpatched in some corporate settings, similar to many ransomware gangs and threat actors.
Alex Delamotte, the senior threat researcher at SentinelOne, outlined the most recent threat to businesses that Sentinel Labs had been tracking since mid-February. CVE-2022-47986 It was initially given a CVSS score of 8.1, but on February 17 it was revised to a severe 9.8 out of 10.
The SentinelOne researcher said:
When compared to Windows, ransomware implementation against Linux is more difficult, especially in large volumes.
The 2.18 MB 64-bit ELF ransomware binary that targets Linux is installed on CentOS servers using a weak variant of IBM Aspera Faspex file server software. Not all Linux data are encrypted with IceFire.
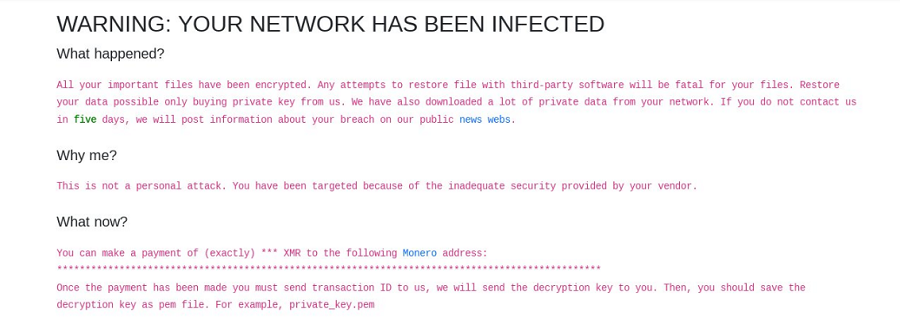
Once they have taken control of the victim’s computer, they will use IceFire ransomware to encrypt data and add the ‘.ifire’ extension to the impacted files. Finally, the ransomware will destroy itself to erase all traces of it.
See more: Russian hacktivists steal data after hacking STALKER 2 creator
IceFire, also known as iFire, is ransomware that creates the “iFire-readme.txt” file, encrypts files, and appends the “.iFire” suffix to filenames.
Attacks by ransomware on people can have a significant effect, resulting in monetary losses, breaches of private information, and emotional stress. However, there is a wide variety of ransom payments; some people only pay $10,000, while others pay millions. The ransomware attack may also result in legal consequences.
Create networks, systems, and backups that are resistant to ransomware. Ensure that access to your special accounts is tightly restricted. Segment your network to stop viruses or malicious users from spreading. All corporate devices should have anti-ransomware solutions.
Author: Vaishnavi Bhujbal
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn