Linux servers are the new targets for ShellBot
A recent campaign that uses various variants of the malware dubbed ShellBot targets poorly maintained Linux SSH servers.
Perl-based ShellBot, also known as PerlBot, is a DDoS bot malware that typically communicates with the C&C host using the IRC protocol. An old piece of malware called ShellBot has been continuously used and is still in use to attack Linux computers.
Threat players use scanner malware to find systems that have SSH port 22 open before installing ShellBot on sites with weak credentials. Simple account credentials that leave the server open to dictionary attacks are a prime illustration of a service that is being poorly managed. The MS-SQL service and Remote Desktop Protocol (RDP) are two prominent instances of attack vectors used against Windows operating systems.
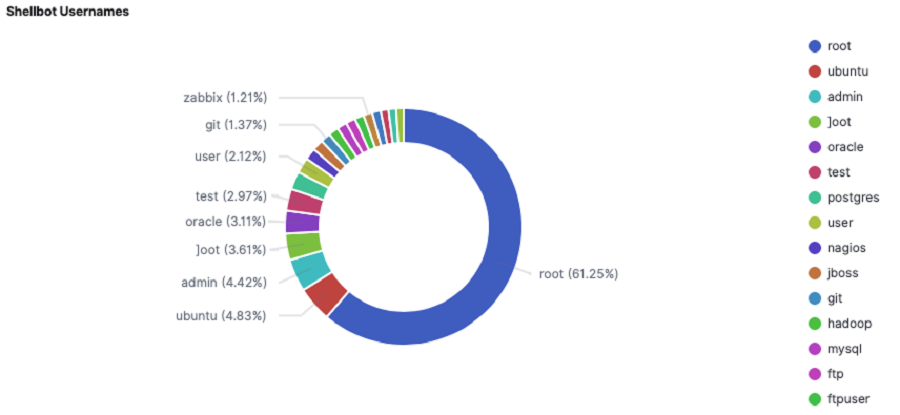
Secure Shell (SSH) services are frequently the focus of attacks on Linux servers. The server is breached and the payload is deployed using a dictionary attack that starts with a list of known SSH passwords, and then it connects to a remote server using the Internet Relay Chat (IRC) protocol.
This includes ShellBot’s capacity to take instructions and execute DDoS assaults while also leaking information that has been collected. Threat actors look for systems where the SSH service is running and launch their dictionary attack using a list of frequently used SSH user credentials.
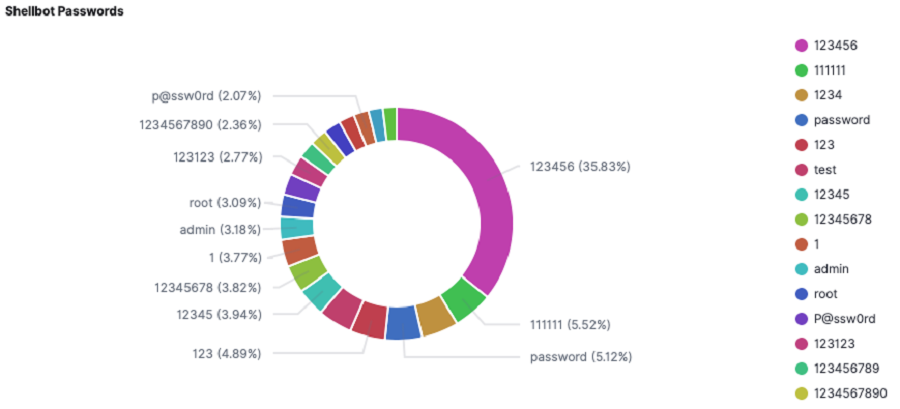
A feature of ShellBot is that it communicates with C&C nodes using the IRC protocol, in addition to being written in Perl. A real-time Internet chat system called IRC was created in 1988. When users log onto specific IRC channels on specific IRC servers, they can instantly communicate with other users who have also joined that channel.
See more: Must Know: QR Code Experimentation by Threat Actors
The bot malware known as IRC Bot makes use of the IRC service to connect to C&C networks.
Linux servers with ShellBot installed could be used as DDoS Bots to launch DDoS assaults against particular targets in response to threat actor commands.
A DDoS’s adverse impacts include:
- Unhappy customers who might never return
- Loss of data
- Loss of income
- The payment of penalties
- Work hours and income lost
- Harm to the company’s image
See more: CISA Warns Industrial Control Systems have critical Vulnerabilities
An organization has a number of choices to lessen the effects of a suspected attack. Organizations should routinely examine their network, servers, and devices as well as perform risk assessments.
Another form of defense is black hole routing, in which the network administrator or internet service provider of a company creates a black hole route and sends data there.
Author: Vaishnavi Bhujbal
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn






