NAS and ESXi Hosts targeted by RTM Locker’s Linux Ransomware
The RTM Locker ransomware strain, which was previously known to target Windows systems, has recently expanded to attack Linux-based systems as well. This new ransomware variant is primarily targeted at Network-Attached Storage (NAS) devices and ESXi servers.
In early 2022, the first known Linux variant of RTM Locker was discovered. Several assaults targeting organizations that rely on Linux systems have been recorded since then. Unlike prior RTM Locker variations, the Linux version has been reported to employ more complex ways to avoid detection and retain persistence on the compromised system.
NAS devices are one of the key targets of this new RTM Locker type. Organizations typically utilize these devices to store and share data across various users and systems. NAS devices are also frequently utilized for backup purposes, making them an attractive target for ransomware attackers.
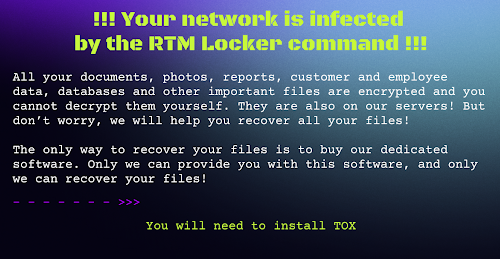
Once infected, the Linux RTM Locker ransomware encrypts all data stored on the NAS system and leaves a ransom note demanding payment in exchange for the decryption key. This attack has the potential to have major ramifications for enterprises, since they may lose access to critical data and information stored on their NAS devices.
This malware also targets ESXi hosts, which are used to run virtual machines in data centers. ESXi hosts are key components of many organizations’ IT infrastructures, and a cyber attack on them might interrupt entire business operations.
See more: FIN7 Hackers Caught Exploiting Veeam Vulnerability
The Linux RTM Locker ransomware strain employs sophisticated tactics to avoid detection and remain on infected systems. It can, for example, use rootkit technology to conceal its presence on the system, making detection and removal difficult. It also employs encryption to secure connection with the command and control server, making it more difficult to track down the attacker and identify the source of the attack.
Organizations should take many precautions to defend themselves from the Linux RTM Locker ransomware. First, they should ensure that all of their systems have the most recent security patches and updates. Strong passwords and multi-factor authentication should also be implemented for all accounts, including those used to access NAS devices and ESXi hosts.
See more: Iranian Hackers Use a Powerless Backdoor to Execute Attacks
The appearance of the Linux edition of RTM Locker ransomware, which targets NAS devices and ESXi hosts, is cause for alarm for organizations that rely on Linux-based systems. To prevent such assaults, solid cybersecurity practices and strong security measures must be followed.
Author: Rajesh Kumar Behera
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn