Python info-stealing malware uses Unicode to evade detection
A malicious Python program on the Python program Index (PyPI) has been found to employ Unicode as a ruse to avoid detection and disseminate malware that steals information.
The onyxproxy package, which may gather and exfiltrate passwords and other crucial information, was delivered to PyPI on March 15, 2023. It received 183 files in total before being deleted later.
These strings, which contain bold and italic typefaces, may still be read, and interpreted by the Python interpreter but only serve to trigger the execution of the stealth malware upon package installation.
The product integrates its malicious activity in a setup script that is packed with thousands of seemingly legit script elements, claims software supply chain security company Phylum.
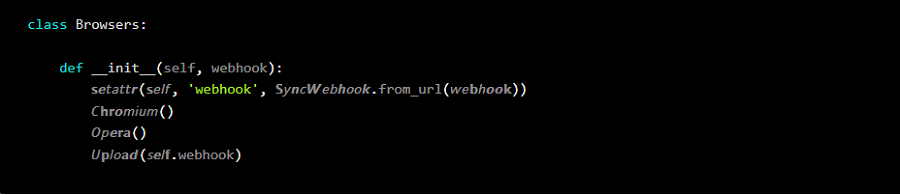
An organization noted that readability was “an evident and immediate benefit of this odd method.” Furthermore, despite what is shown, the code still functions as intended.
Must Know: QR Code Experimentation by Threat Actors
This is made feasible using homoglyphs, or Unicode versions of what seems to be the same character, to hide its actual colors (for example, self vs. self) among seemingly innocent functions and variables.
Researchers Nicholas Boucher and Ross Anderson of Cambridge University first revealed how to use Unicode to inject vulnerabilities into code base in an attack method known as Trojan Source. While showing obvious traces of copy-paste attempts from other sources, the approach makes up for what it lacks in complexity by producing a unique piece of obfuscated code.
See more: CISA Warns Industrial Control Systems have critical Vulnerabilities
This technological breakthrough demonstrates threat actors’ ongoing efforts to develop new techniques for getting beyond string-matching-based protections by using “how well the Python interpreter uses Unicode to hide malware.”
The three new malicious Python packages Aiotoolbox, asyncio-proxy, and pycolorz were discovered by the Canadian cybersecurity company PyUp. They were designed to accept obfuscated code from a remote server and were downloaded over 1,000 times combined.
Author: Animesh Tripathy and Harsh Vikram Shahi
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn






