Redline Info-stealer spread through Document signing providers
Attackers frequently try to utilize legitimate online document providers like Adobe PDF to transmit malware. In another instance, they are misusing Adobe Acrobat Sign, a legitimate document signing tool to spread the Redline information stealer.
The e-signature service Adobe Acrobat Sign enables users to exchange documents with intended users for their digital signatures after uploading them to the cloud. Customers can upload their files to Adobe’s public servers at eu1.documents.adobe[.]com/public/ as it is available free of cost. With Adobe’s email-based notification service, users may share submitted documents with particular recipients once they’ve been uploaded. While sharing their papers, users of this service have the option to add personalised messages.
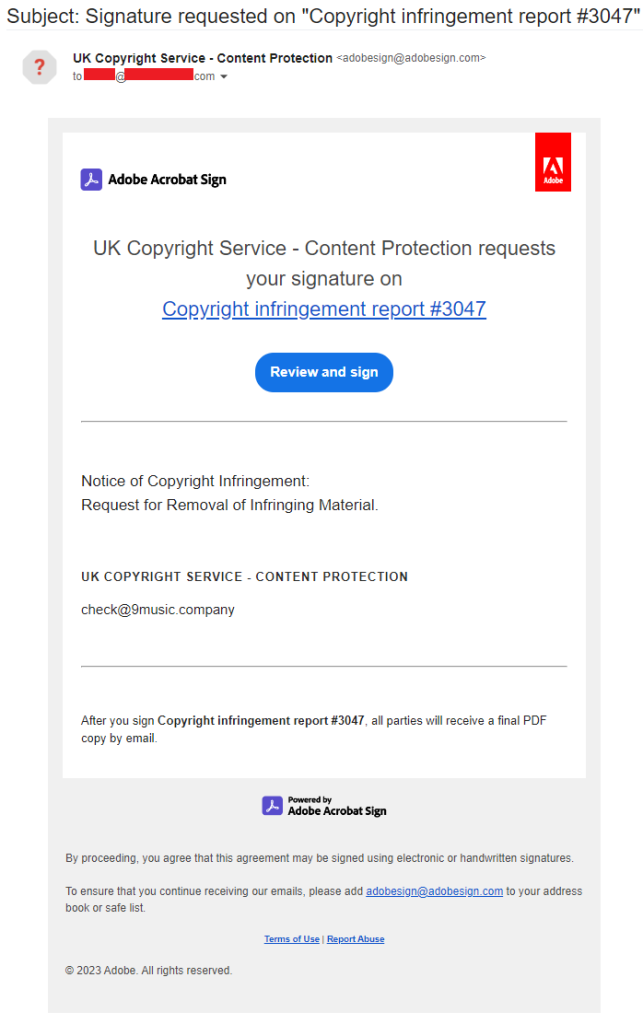
Avast researchers discovered that attackers are misusing this service to spread Redline. They submit a document with a link to their website and use a phoney email to sign up for the service. They send a fake email from Adobe (adobesign@adobesign[.]com) inviting potential victims to evaluate and sign the document. The attackers’ customized directions in the email advises the recipient to study the paper carefully before signing it. The victims are directed to another website by the link in the document that is secured by a hardcoded CAPTCHA. Victims are then prompted to download a ZIP file containing Redline.
See more: Karnataka Remote Sensing Applications Centre hacked by Lockbit
Focused attacks
- Attackers repeatedly attempt to spread malware to the same intended victim making the attacks extremely targeted.
- In one such instance, a well-known YouTube channel owner reported receiving a fraudulent email purporting to be a copyright violation warning from a record label (uploaded on Adobe Acrobat Sign).
- When the owner of the YouTube channel did not click on the link, the attackers tried again by sending a different bogus message using a different document signing provider, dochub[.]com.
- All of the efforts ultimately lead the victim to the download page for Redline.
Recent misuse of cloud services
- Many attackers have targeted cloud-based services in recent months to carry out a number of nefarious tasks, including malware dissemination and cryptojacking.
- Last month, a mystery hacking gang known as Nevada Group targeted thousands of cloud servers around the United States and Europe by taking advantage of a simple security flaw.
- At the same time, the Tsunami IRC bot and a customized cryptominer were being used by the China-based 8220 Gang to attack inadequately protected cloud services.
See more: How to detect hardware trojans in microchips
In order to directly access the target’s mailbox through valid notification channels, phishing attackers have started to exploit legitimate cloud-based services like Adobe Acrobat Sign as cover.
Users are advised to use extreme caution when clicking on links they receive from unidentified sources. Moreover, scan every information downloaded from the internet with a reliable antivirus program before running it on the computer.
Author: Twinkle Sahoo
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn






