Rilide Malware Targeting Chrome-Based Browsers to Steal Crypto
Rilide is a brand-new piece of malware that preys on Chromium-based web browsers to steal cryptocurrency and harvest sensitive information by disguising itself as an apparently trustworthy extension.
Rilide malware impersonates a legal Google Drive extension and gives threat actors access to a variety of malicious functions, such as monitoring.
Trustwave SpiderLabs Research stated in a report provided to The Hacker News that attackers were “browsing history, taking screenshots, and injecting malicious scripts to withdraw money from various cryptocurrency exchanges.”
Additionally, the stealer malware has the ability to show forged dialogue boxes to trick users into entering a two-factor authentication code to extract digital assets.
The malicious browser extension was installed as a result of two separate operations, according to Trustwave, involving the Ekipa RAT and Aurora Stealer.
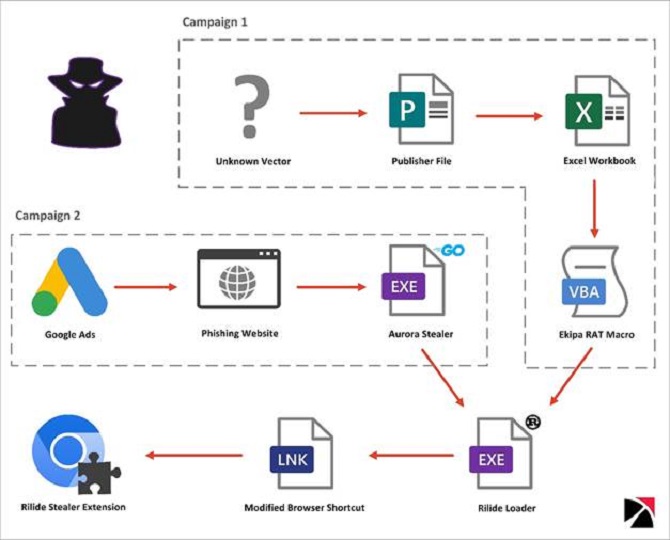
In contrast to Ekipa RAT, which spreads through malicious Microsoft Publisher files, Aurora Stealer uses rogue Google Ads as its distribution vector—a strategy that has grown more popular in recent months.
Both attack chains make it easier to run a Rust-based loader, which in turn changes the LNK shortcut file for the browser and launches the add-on using the “–load-extension” command line option.
See more: Ukrainian Police busted Phishing Gang that stole $4.33 Million
Rilide’s precise ancestry is unclear, but Trustwave claimed to have located a threat actor’s advertisement for the sale of a botnet with similar features in a hidden forum post from March 2022.
Following what appears to be an unresolved payment dispute, a part of the malware’s source code has since made its way to the forums.
One noteworthy feature implemented in the exposed source code is the ability to exchange cryptocurrency wallet addresses in the clipboard with an actor-controlled address that is hard-coded in the sample.
See more: Supply Chain Threats Exposed by Azure Pipelines Vulnerability
In addition, the Rilide code provided a command-and-control (C2) address that identified numerous GitHub repositories owned by a person by the name of Gulantin that contained loaders for the extension.
As per Trustwave
Rilide Stealer is a prime example of the increasing sophistication and dangers posed by malicious browser extensions.
The upcoming implementation of manifest v3 may make it harder for threat actors to operate, but it is unlikely to completely resolve the problem because most of the functionalities used by Rilide will still be accessible.
Author: Sanghamitra Sethy
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn






