Synopsys identifies new vulnerability in Pluck CMS
Synopsys, a firm specializing in software security, has identified a fresh remote code execution (RCE) vulnerability in the Pluck CMS system. Pluck is a PHP-based content management system (CMS) created for creating and maintaining your own website. Pluck was designed with simplicity and ease of use in mind, making it ideal for managing a tiny website.
New RCE weakness discovered by Synopsys Cybersecurity Research Center could expose Pluck Content Management System to risk.
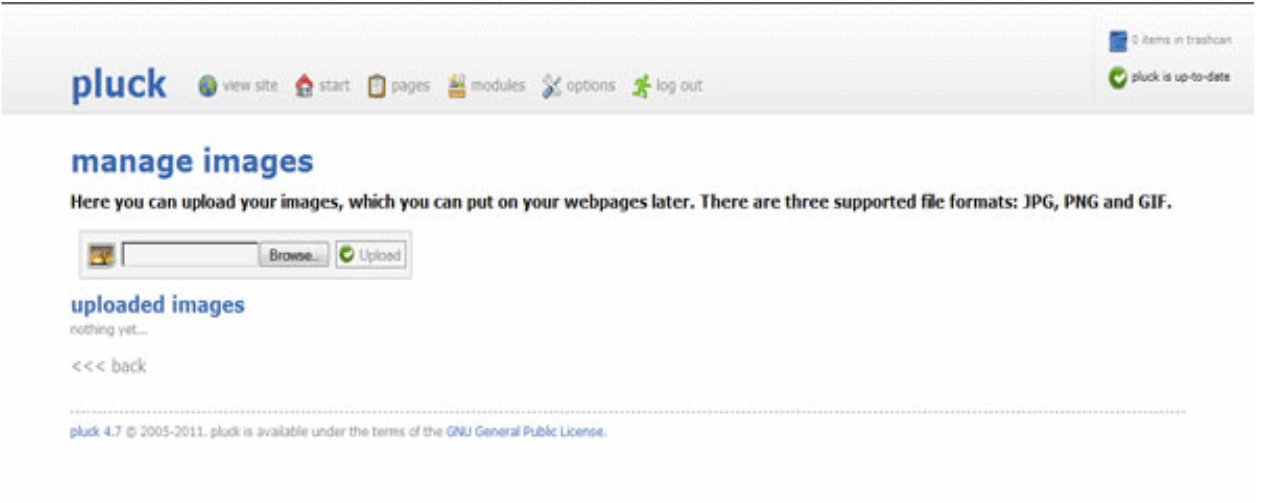
There is a “albums” section in Pluck CMS. Images can be added to web pages throughout the site by using albums, which are used to make collections of images. JPEG, PNG, and GIF file types can be uploaded to albums; these file types go through a normalization procedure before being made accessible on the website.
But not everything in the system is as it seems. Due to the lack of file extension validation, it is possible to submit a modified JPEG payload with an embedded PHP web-shell.
See more: Twitter source code leaked online on Github
Users of Pluck are thus vulnerable to attacks, as are the communities they create with the CMS. A threat actor may choose to go directly to the underlying web server if they wish to commit RCE on it.
Create a sample album in the albums module after authenticating through the web portal. Simple web-shell embedding methods cannot be used because images uploaded to an album are subject to normalization via functions from the PHP-GD graphics library.
See more: Sun Pharma business suffers after a ransomware attack
However, by using the Jellypeg tool to generate such a payload and upload it with an executable file extension, it is possible to embed a web-shell into a JPEG image that will withstand this normalization. (.php, .phar, etc.). Direct access to the submitted file enables RCE.
By taking advantage of this flaw, an attacker would be able to execute any instructions on the operating system of the web server that is running Pluck CMS.
Author: Vaishnavi Bhujbal
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn