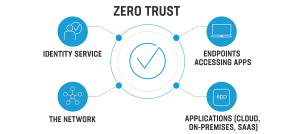
Key components of zero trust network access system – ZTNA
Key components of zero trust network access system – ZTNA Zero trust network access (ZTNA) is a security model that assumes that all network traffic

Key components of zero trust network access system – ZTNA Zero trust network access (ZTNA) is a security model that assumes that all network traffic
© 2024 -Latest Hacking Updates | Site Designed and Developed by – Traffic Tail

Subscribe to our weekly newsletter below and never miss the latest News.