The SolarWinds attack and details we should know
One of the most significant cyber security news stories in recent years was the SolarWinds attack. This sophisticated attack on a software company, which was uncovered in late 2020, affected numerous government agencies, Fortune 500 companies, and other organizations worldwide.
The attack on SolarWinds, a software company that provides services to government and corporate clients, was discovered by cybersecurity firm FireEye, which itself had been targeted in a similar attack. FireEye’s investigation revealed that SolarWinds had been compromised by a group of hackers believed to be backed by the Russian government.
The SolarWinds attack was a supply chain attack, which means that the attackers were able to infiltrate the software supply chain and insert malicious code into a software update that was then distributed to SolarWinds clients. This allowed the attackers to gain access to the networks of SolarWinds clients, bypassing traditional security measures and operating undetected for months.
The scope of the SolarWinds attack was massive. It is estimated that up to 18,000 organizations may have been affected, including the US Department of Homeland Security, the Treasury Department, and the Department of Justice, as well as major companies such as Microsoft, Cisco, and Intel. The attackers were able to steal sensitive data, including emails, documents, and credentials, and potentially disrupt critical infrastructure.
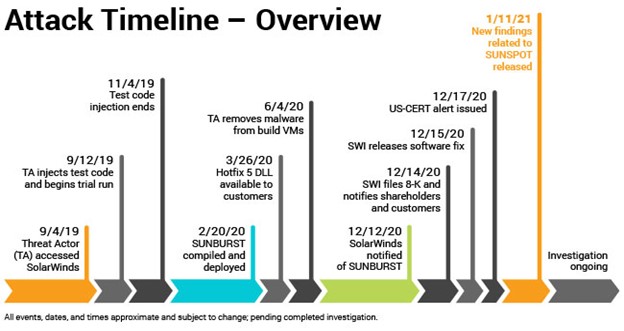
The SolarWinds attack has highlighted the need for greater cybersecurity measures, particularly in supply chain security. The attackers were able to exploit vulnerabilities in SolarWinds software development process, which allowed them to insert malicious code into the software update without being detected. This has led to calls for greater transparency and security in the software development process, as well as improved detection and response capabilities.
The SolarWinds attack also underscores the growing threat posed by nation-state hackers. State-sponsored hackers have the resources and expertise to carry out sophisticated attacks, and they are increasingly using cyber attacks as a means of espionage and political influence. This has led to increased tensions between countries, with accusations of cyber espionage and retaliation.
See more: Ukraine DDoS assault confirmed by the Ministry of Defense
The SolarWinds attack serves as a wake-up call for the cybersecurity industry and the need for improved security measures. While the attack was sophisticated and well-planned, it was not entirely unforeseeable. The lessons learned from the SolarWinds attack must be applied to improve the security of supply chains, increase transparency in the software development process, and improve detection and response capabilities. Only then can we hope to prevent similar attacks in the future.
The SolarWinds attack has also raised questions about the role of regulation in cybersecurity. Some experts have argued that there needs to be greater government oversight and regulation of the software industry to ensure that companies are held accountable for security breaches. Others argue that regulation could stifle innovation and that the private sector is better equipped to develop effective cybersecurity measures.
Another important lesson from the SolarWinds attack is the importance of collaboration and information sharing among cybersecurity professionals. The discovery of the attack was made possible by FireEye sharing information with other cybersecurity firms, which helped to identify the scope and scale of the attack. This highlights the need for greater collaboration and information sharing among cybersecurity professionals, as well as the need for organizations to be more transparent about security breaches and share information with their peers.
See more: Ransomware led to multiple DISH Network outages
The SolarWinds attack has also highlighted the need for greater investment in cybersecurity. Many organizations are underinvesting in cybersecurity, either due to budget constraints or a lack of awareness of the risks. However, as the SolarWinds attack demonstrates, the costs of a security breach can be far higher than the cost of investing in cybersecurity measures.
Finally, the SolarWinds attack serves as a reminder that cybersecurity is not just a technical issue but also a strategic issue. Cybersecurity risks must be factored into organizational decision-making and risk management processes, and cybersecurity professionals must be given a seat at the table when decisions are made that could impact the security of the organization.
Author: Yogita Bhoi
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn






