Unpatched SonicWall SMA devices targeted by Chinese hackers
Unpatched SonicWall Secure Mobile Access (SMA) 100 appliances are the target of a hacking campaign with possible Chinese connections that aims to install malware and establish long-lasting persistence. In a technical report released this week, cybersecurity firm Mandiant stated that the malware can steal user credentials, grant shell access, and endure firmware upgrades.
Under the unclassified identifier UNC4540, the Google-owned incident response and threat intelligence company is monitoring the activity. The malware is designed to give the attacker privileged access to SonicWall devices. It consists of a group of bash scripts and a single ELF binary known as a TinyShell backdoor. The malware allows the adversary to steal cryptographically hashed credentials from all users who are currently logged in, suggesting that the custom toolset’s main goal is credential theft. It also grants the compromised device shell access.
The ability of the attacker to create custom malware that can withstand firmware updates and keep a foothold on the network, as well as their in-depth knowledge of the device software, were also criticized by Mandiant. Although the precise first point of entry used in the attack is unknown, it is believed that the malware was most likely installed on the devices, in some cases as early as 2021, by exploiting known security flaws.
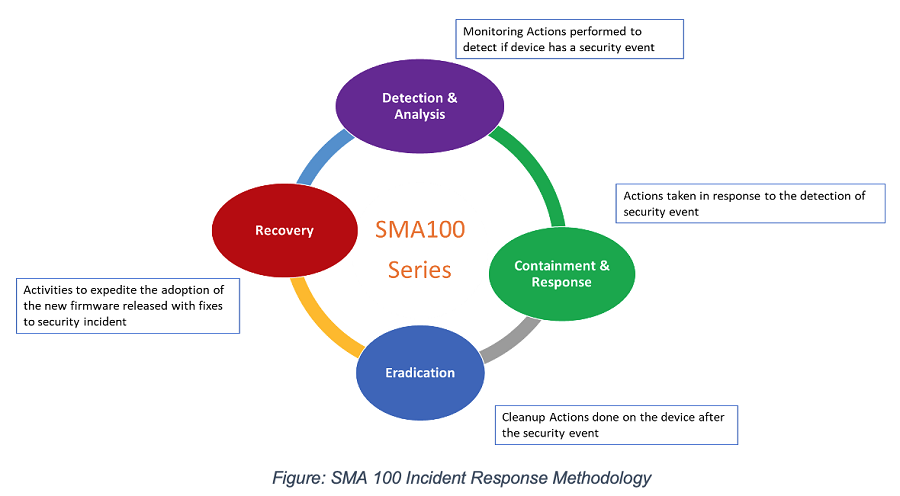
In response to the information being made public, SonicWall has released updates (version 10.2.1.7) that add fresh security features like File Integrity Monitoring (FIM) and anomalous process identification.
This development occurs almost two months after it was discovered that a different China-nexus threat actor was using a Fortinet Fort iOS SSL-VPN vulnerability that has since been patched as a zero-day attack vector against a European government organization and an African managed service provider (MSP).
To fully penetrate an enterprise, Chinese attackers have recently used several zero-day exploits and malware for a variety of internet-facing network appliances, according to Mandiant.
Author: Sarthak Murtadak
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn






