BATLOADER delivers Vidar Stealer and Ursnif using Google ads
Malware downloaders such as BATLOADER and Vidar Stealer have been observed using Google Ads to deliver secondary payloads. Batloader is usually infiltrated via malicious websites that pretend to be legitimate software or applications. Victims can be redirected to these websites via malvertising techniques and fake comments on forums that contain links to Batloader distribution websites.
As reported by a cybersecurity agency, malicious ads spoof apps and services such as Adobe, OpenAPI’s ChatGPT, Spotify, Tableau, and Zoom. The BATLOADER is a loader that distributes a range of malware, including information stealers, banking malware, Cobalt Strike, and even ransomware. The BATLOADER operations use software impersonation tactics to deliver malware.
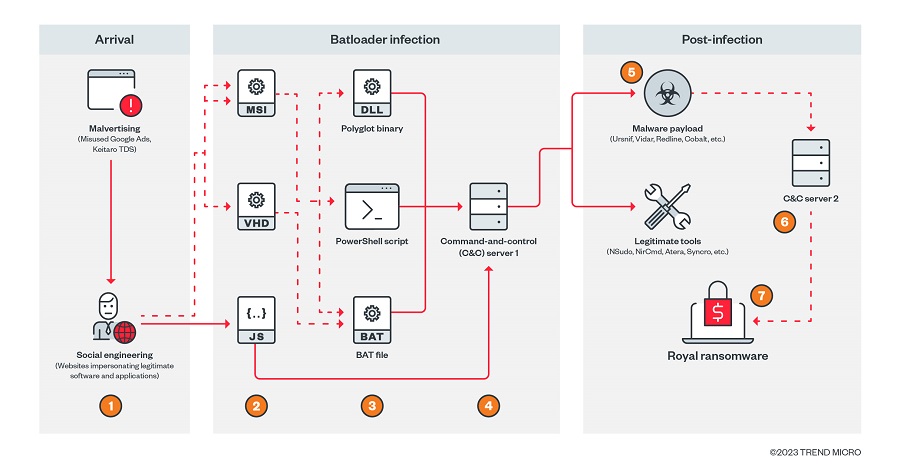
Users searching for software can trigger the infection sequence by clicking on a rogue ad on the Google search results page when they click a lookalike website hosting Windows installers disguised as legitimate apps. As soon as these MSI installers are launched from a remote server, Python scripts containing the BATLOADER payload are executed. In December 2022, MSI installer packages were used to run PowerShell scripts to download stealer malware, which marked a slight shift in attack chains. BATLOADER samples analyzed by the security agency have also revealed added capabilities that enable it to gain entrenched access to enterprise networks.
The cyber security agency said:
BATLOADER continues to evolve and improve since its debut in 2022. BATLOADER targets various popular applications in order to imitate them. This is not a coincidence, as these applications are often found in corporate networks and thus would provide more valuable starting points for monetization through fraud or keyboard intrusion.
According to the research, Batloader is a highly evasive and evolutionary malware family that can deploy various types of malware, including loaders, bots, and ransomware. Batloader tricks its victims by using various malvertising and social engineering techniques to spread malicious payloads.
See more: The SolarWinds attack and details we should know
Batloader is a prime example of modern malware and a modular threat. Protecting systems from it requires a robust and layered solution that provides a common view from a central location. Trend Micro Vision One is a technology that collects and automatically correlates data across multiple layers of security-from email and endpoints to servers, cloud workloads, and networks.
Author: Kashyap Kumar Mishra
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn






