Go-Based Hinata Bot Abuses Vulnerabilities for DDoS Attacks
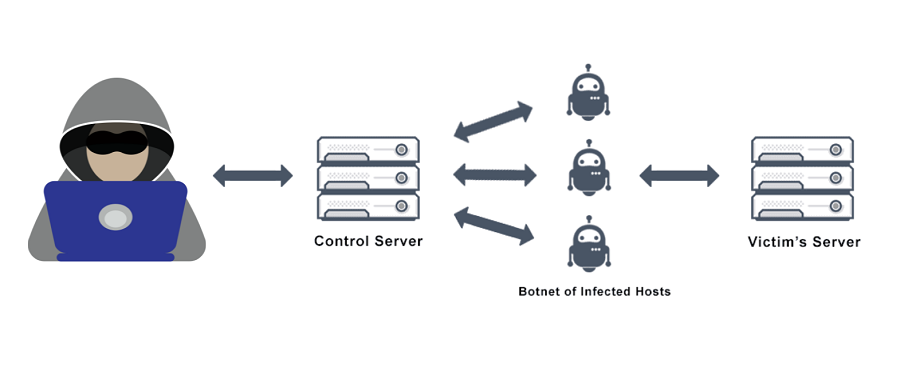
The most recent botnet targeted at distributed denial-of-service (DDoS) attacks is a Go-based malware network. The Security Intelligence Response Team (SIRT) of Akamai researchers has identified a fresh Go-based DDoS-targeted botnet. The moniker “Hinata” malware appears to have been chosen by the malware creator in honour of a Naruto character. It has the moniker “Hinata Bot.”
Throughout the first three months of 2023, Hinata Bot was observed being distributed, and its creators and operators are constantly updating it. The sample, which took use of outdated vulnerabilities and shoddy credentials, was found in HTTP and SSH honeypots Exploiting the tiny SOAP service is one of the infection attempts that have been seen.
The most recent iteration of the botnet is restricted to only HTTP and UDP, although earlier iterations used protocols like HTTP, UDP, TCP, and ICMP to conduct DDoS assaults. The reasons for eliminating the other two protocols are currently unknown.
Akamai, conducted 10-second attack tests using HTTP and UDP, and later disclosed that the HTTP flood generated 3.4 MB of packet capture data and sent approx. 20,430 HTTP requests. On the other hand, the UDP flood generated 6,733 packets, totalling 421 MB of packet capture data.
A UDP flood would peak at more than 3.3 terabits per second (Tbsp.) in a fictitious real-world attack with 10,000 bots, creating a potent volumetric attack. Around 27 gigabits of traffic per second would be produced by an HTTP flood (Gbps).
With this evolution, it now ranks as the newest threat among a long list of new Go-based dangers, like GoBruteforcer and KmsdBot.
See more: HMIS portal breached exposing data of 40 million patients
Attackers have taken advantage of Go’s high performance, simplicity of multi-threading, support for multiple architectures, and operating system cross-compilation, but it’s also probably because it adds complexity to the compilation process, making it harder to reverse engineer the resulting binaries, according to Akamai.
Akamai researchers have discovered and reverse engineered a new botnet: HinataBot.
🔵 actively being updated
🟠 discovered in HTTP and SSH honeypots abusing old vulns and weak creds
🔵 based on Mirai
🟠 seeks to achieve DDoS
🔵 Go-basedFull write-up:https://t.co/54bBahPPnk pic.twitter.com/jmuScVOxVF
— Akamai Security Intelligence Group (@akamai_research) March 16, 2023
The findings coincide with Microsoft’s disclosure that, in 2022, TCP attacks—which accounted for 63% of all attack traffic—became the most common type of DDoS attack, followed by UDP floods and amplification attacks (22%) and packet anomaly attacks (15%).
See more: SILKLOADER malware is a new weapon to avoid detection
DDoS attacks are anticipated to increase due to the appearance of new malware strains that are capable of targeting IoT devices and taking control of accounts to gain unauthorized access to resources, in addition to being used as distractions to disguise extortion and data theft.
The Azure Network Security Team of the IT giant said: “With DDoS attacks growing more common, smart, and affordable to launch, it’s important for enterprises of all sizes to be proactive, keep protected all year long, and build a DDoS response strategy.
Author: Priyanka Sonawane
We hope you found the article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn