SILKLOADER malware is a new weapon to avoid detection
A new piece of malware created to load Cobalt Strike onto compromised computers has been used by threat activity clusters connected to the Chinese and Russian cybercriminal ecologies. The malware, known as SILKLOADER by a cybersecurity firm, uses DLL side-loading strategies to distribute paid adversary simulation software.
The development comes as threat actors are being forced to look for alternate solutions or come up with new ways to spread the framework to dodge detection due to better detection capabilities against Cobalt Strike, a genuine post-exploitation tool used for red team operations.
According to security researchers, the most frequent of these involve adding complexity to the automatically generated beacon or stager payloads by using packers, crypters, loaders, or comparable approaches.
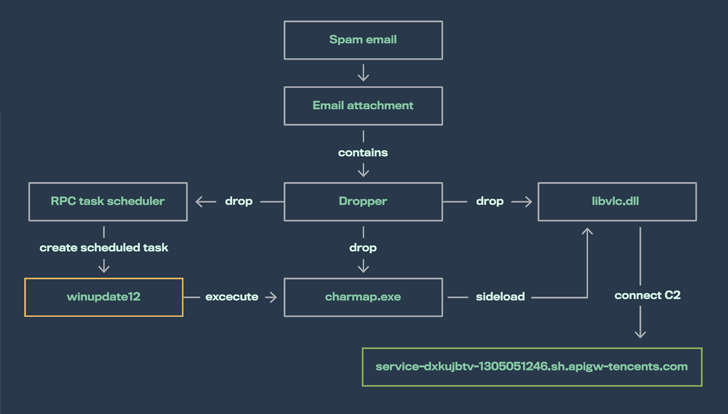
SILKLOADER joins other recently discovered loaders that incorporate Cobalt Strike components, such as KoboldLoader, MagnetLoader, and LithiumLoader. It also has similarities to LithiumLoader in that both use the DLL side-loading technique to sabotage a trustworthy application to launch a different, malicious dynamic link library (DLL).SILKLOADER accomplishes this by dropping specially designed libvlc.dll files together with a genuine but renamed VLC media player code (Charmap.exe).
See more: CISA identifies Adobe ColdFusion Vulnerability exploited globally
Following an investigation of “many human-operated intrusions” that targeted numerous entities covering a wide spectrum of enterprises in Brazil, France, and Taiwan in Q4 2022, the security organization claimed to have discovered the shellcode loader. Even though these attempts failed, it is believed that they served as a prelude to ransomware deployments because the strategies and equipment used “heavily overlapped” with those credited to the creators of the Play ransomware.
An unknown French social welfare institution was the target of one attack in which the threat actor used a compromised Fortinet SSL VPN equipment to stage Cobalt Strike beacons and obtain access to the network. For several months, the threat actor “kept a foothold in this organization,” according to a security firm. They engaged in actions such as credential theft and discovery during this time, which was followed by the deployment of several Cobalt Strike beacons.
See more: Unpatched SonicWall SMA devices targeted by Chinese hackers
The adversary then moved to utilize SILKLOADER to avoid detection and deliver the beacon payload when this effort failed. In recent months, attacks using Quantum ransomware, GootLoader, and the IcedID malware have been connected to another loader known as BAILLOADER, which is also used to disseminate Cobalt Strike beacons.
The crypto Tron, which has been used by several adversaries to spread the malware Emotet, TrickBot, BazarLoader, IcedID, Conti ransomware, and Cobalt Strike, is claimed to share similarities with BAILLOADER.
As a result, several threat actors may collaborate to service numerous breaches using various techniques by sharing Cobalt Strike beacons, cryptos, and infrastructure provided by third-party affiliates. In other words, threat actors based in Russia are probably being provided SILKLOADER as an off-the-shelf loader through a Packer-as-a-Service scheme.
According to the security firm, “This loader is either being delivered directly to ransomware groups or maybe via groups delivering Cobalt Strike/Infrastructure-as-a-Service to trusted affiliates. After the Conti group’s claimed collapse, “the majority of these affiliates appear to have been a part of or to have had close working contacts with the Conti group, its members, and its children.”
The company’s analysis of SILKLOADER samples reveals that early iterations of the malware date back to the beginning of 2022, with the loader being used exclusively in various assaults aimed at victims in China and Hong Kong. Around July 2022, the focus shifted from East Asian targets to other nations, including Brazil and France. Since then, all SILKLOADER-related incidents have been linked to Russian cybercriminal operators. As a result, it has been suggested that “SILKLOADER was originally built by threat players functioning within the Chinese cybercriminal ecosystem” and that “the loader was employed by the threat actors within this nexus at least as early as May 2022 until July 2022.
Author: Sayyam Gangwal
We hope you found the article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn






