CISA identifies Adobe ColdFusion Vulnerability exploited globally
Based on the evidence of active exploitation, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) added an Adobe ColdFusion security vulnerability to its Known Exploited Vulnerabilities (KEV) list on March 15.
CVE-2023-26360 (CVSS score: 8.6) is the significant weakness in question, which a threat actor might use to execute arbitrary code.
The inappropriate access control vulnerability in Adobe ColdFusion, according to CISA, permits remote code execution.
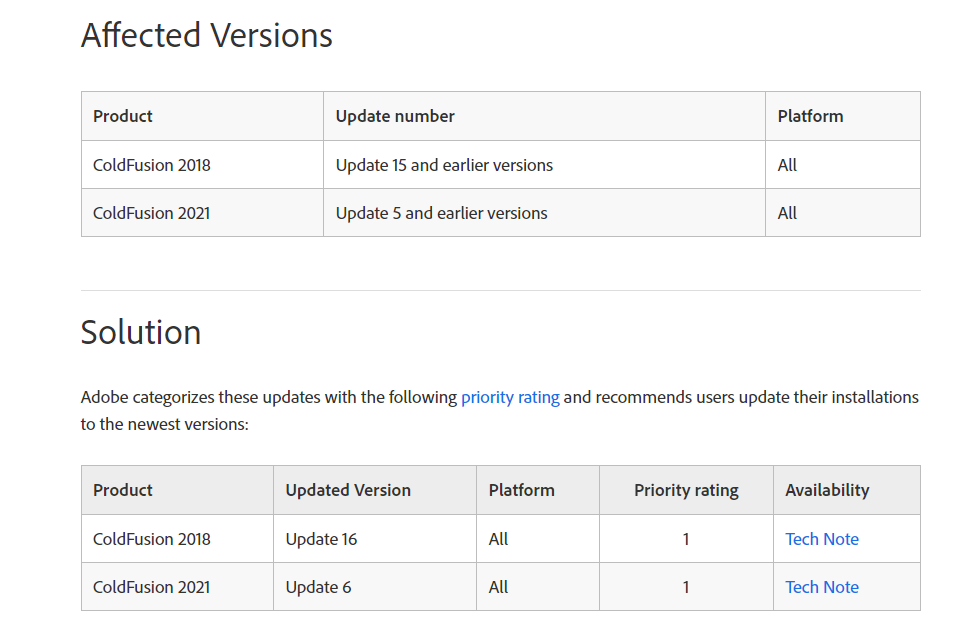
ColdFusion 2018 (Update 15 and previous versions) and ColdFusion 2021 are both affected (Update 5 and earlier versions). Version Update 16 and Version Update 6 both addressed it when they were released on March 14, 2023, respectively.
The CVE-2023-26360 vulnerability also affects installations of ColdFusion 2016 and ColdFusion 11, both of which are no longer maintained by the software provider as they have reached end-of-life (EoL).
While Adobe also announced the ColdFusion 2021 and 2018 March 2023 Security Updates in a separate blog post, it omitted to indicate that the patched security vulnerabilities were also actively being used in the wild.
In a comment to Adobe’s blog post, Charlie Arehart, one of the two security researchers credited with finding and disclosing the CVE-2023-26360 bug, warned ColdFusion administrators of the real significance of the security patches and the urgency with which they must be patched.
See more: Delhi Police collaborates with Truecaller to combat cyber fraud
Administrators are urged to implement the security configuration settings described in the lockdown instructions for ColdFusion 2018 and ColdFusion 2021 as soon as possible (within 72 hours, if practicable), along with the security upgrades.
Adobe no longer offers security fixes for versions that are out of support, despite the fact that the bug also affects installations of ColdFusion 2016 and ColdFusion 11.
See more: Unpatched SonicWall SMA devices targeted by Chinese hackers
Adobe stated in a warning that it is aware of the weakness being “exploited in the wild in extremely limited assaults,” despite the fact that the precise specifics of the attacks’ nature remain unclear.
By April 5, 2023, FCEB organizations must implement the changes in order to protect their networks from potential threats.
This “severe” hole might lead to “arbitrary code execution” and “arbitrary file system read,” according to Charlie Arehart, a security researcher who discovered and reported the flaw with Pete Freitag.
Author: Sanghamitra Sethy
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn






