Government and CIS energy targeted by YoroTrooper cyberspies
Government, CIS energy, and international organizations in Europe have been the target of a cyber espionage operation that has been ongoing since at least June 2022 by a previously unknown Russian-speaking threat actor known as “YoroTrooper”.
On Tuesday, YoroTrooper was discovered by Cisco Talos’ cybersecurity specialists as a new online threat actor. The threat actor customizes the emails and attachments to the particular target organization and employs phishing as the initial attack vector.
The researchers in Cisco Talos said that, the threat actor has compromised accounts of a critical European Union agency engaged in healthcare, the World Intellectual Property Organization (WIPO), and various European embassies.
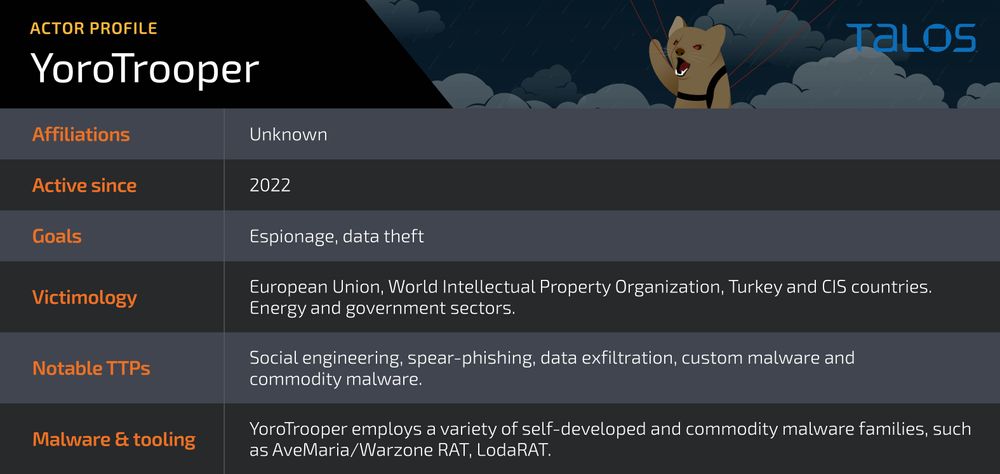
Based on analysis, they added that the primary targets are government or energy institutions in Azerbaijan, Tajikistan, Kyrgyzstan, and other Commonwealth of Independent States (CIS).
Credentials from numerous apps, browser histories and cookies, system information, and screenshots are just a few of the items taken from successful compromises. YoroTrooper employs a combination of Python-based adware, remote access trojans, and standard and specialized information stealers.
See more: LastPass Hack in trouble after failure to upgrade flex software
Due to the victimology patterns and the existence of Cyrillic snippets in some of the implants, it is thought that the threat actor speaks Russian. According to their analysis of this danger actor’s tactics, techniques, and procedures (TTPs), espionage is their primary driving force.
YoroTrooper uses a combination of commercial and open source stealth programmes like Ave Maria (also known as Warzone RAT), LodaRAT, Meterpreter, and Stink to collect data. Phishing emails with malicious LNK attachments and fake PDF papers are how the infection spreads.
The use of LodaRAT is significant because it shows that numerous operators are using the malware, despite the fact that Kasablanka, another group, is responsible for its attribution. Kasablanka has also been seen distributing Ave Maria in recent campaigns aimed at Russia.
See more: IBM Aspera Faspex Exploited by the IceFire Ransomware
Nuitka makes it possible to spread the payloads as stand-alone programmes without having to install Python on the target device.
The customised RAT allows the execution of arbitrary commands on the infected device and uses Telegram for communication with command and control servers and data exfiltration. As of the beginning of March, the most recent Stink Stealer 2.1.1 version has an autostart configuration option that will make a link in the victim profile’s startup folder with the name “Windows Runner.”
YoroTrooper’s sponsors or connections are unclear, and its origin is unknown. This shows a rise in the threat actor’s efforts, which are probably the result of effective breaches throughout the campaign.
Author: Vaishnavi Bhujbal
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn






