New Version of Prometei Bot Infects Over 10K Systems worldwide
Since November 2022, more than 10,000 systems have been compromised by an improved version of the Prometei botnet virus. Most of the victims have been identified in Brazil, Indonesia, and Turkey, indicating that the infections are both opportunistic and geographically indiscriminate.
Prometei is a modular botnet that was originally discovered in 2016 and has a wide range of components and proliferating strategies. Also, it distinguishes out for avoiding Russia, indicating that the threat agents behind the operation are probably situated there.
Financial gain is the primary driving force behind the cross-platform botnet, which uses its host pool of infected computers to mine crcryptocurrenciesnd gather login information. The most recent Prometei version (known as v3) enhances its current characteristics to defy forensic investigation and further bury its access on target computers.
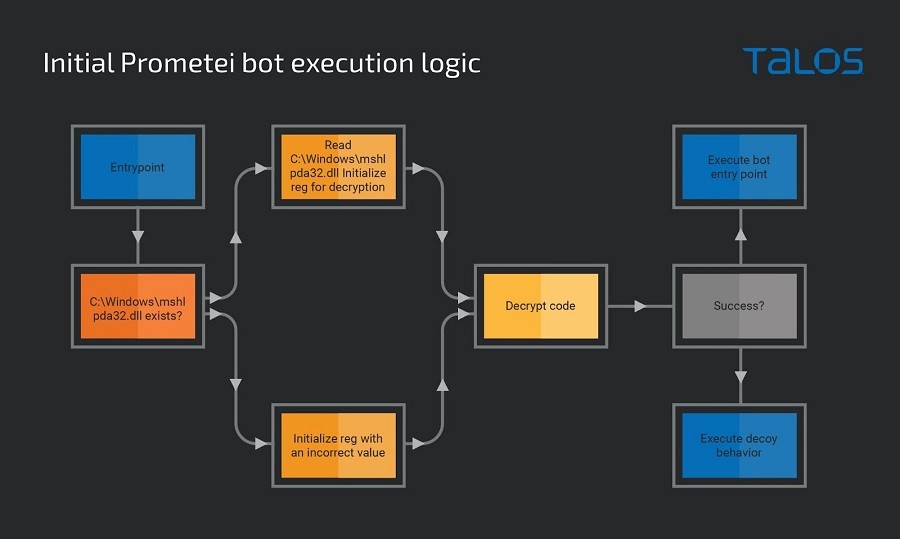
Following a successful foothold, a PowerShell command is run to download the botnet payload from a remote server. Here is how the attack process plays out. The real crypto-mining payload and other system auxiliary components are then retrieved using Prometei’s main module.
Several of these support modules serve as distributor programs created to distribute the virus using Server Message Block (SMB), Secure Shell (SSH), and Remote Desktop Protocol (RDP).
See more: YouTube tutorials produced by AI spreading info-stealing malware
Another important feature of Prometei v3 is that it developed its command-and-control (C2) infrastructure using a domain generation algorithm (DGA). It also has a self-updating system and an enhanced range of instructions for stealing sensitive information and taking control of the host.
The malware deploys an Apache web server that’s packed with a PHP-based web shell, and that is capable of executing Base64-encoded instructions and carrying out file uploads. This recent addition of new capabilities that the Prometei operators are continuously updating the botnet and adding functionality.
Author: Sanjana Amale
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn






