Play Ransomware Group Adds New Tools to Harvest More Data
Ransomware attacks have grown more common in recent years, with cybercriminals employing advanced ways to extort money from organizations and individuals. One of the most infamous ransomware organizations, known as “Play,” has lately added two new weapons to its arsenal, potentially making its operations even more destructive.
The first tool is named “Data Stealer,” and it is meant to steal sensitive data from victims’ machines. Passwords, bank details, and other personal information can be sold on the dark web or used to commit identity theft. Data Stealer is thought to be highly adept at circumventing security protections like as firewalls and antivirus software, allowing Play to access and retrieve important data more easily.
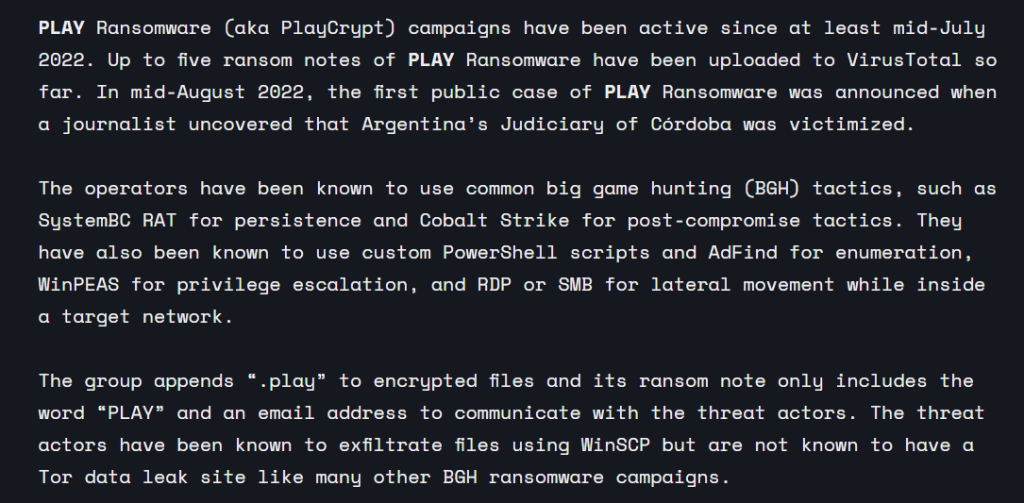
The second program, “FileHunter,” is intended to look for specific files on a victim’s computer. Files containing sensitive information, such as financial data or private business papers, may fall into this category. File Hunter can swiftly scan massive amounts of data, which means Play may possibly access and extract vital information in a matter of minutes.
These new capabilities are simply the most recent illustration of how ransomware gangs like Play are upgrading their techniques. These gangs have gotten more sophisticated in recent years, employing modern tactics such as social engineering and machine learning to target their victims. They also regularly utilize encryption to encrypt a victim’s data, rendering it inaccessible without paying a ransom.
See more: Akamai to Buy Startup Neosec for API Detection and Response
A ransomware assault may be disastrous for both organizations and people. Not only may it result in the loss of vital data, but it can also cause considerable financial and reputational harm. Ransomware assaults have even resulted in the shutdown of enterprises in rare situations.
See more: Goldoson Android malware affects 60 apps with 100M installs
Individuals and corporations should take a variety of actions to protect themselves against these sorts of assaults. This involves backing up data on a regular basis, using secure passwords, and keeping antivirus software up to date. It is also critical to be wary of unusual emails or other forms of contact, since they are frequently used by ransomware gangs to dupe their victims.
Finally, the addition of Data Stealer and FileHunter to Play’s arsenal is a cause for concern for both enterprises and people. These technologies have the potential to make ransomware assaults much more severe, emphasizing the importance of strong cybersecurity safeguards and enhanced awareness in the face of such threats.
Author: Priyanka Priyadarshini Dwibedy
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn






