Top 7 Attacks on Active Directory: What You Need to Know
Active Directory is a directory service developed by Microsoft that allows administrators to manage and secure access to network resources. It is used by organizations to store and manage user, computer, and network resources, and to provide secure access to these resources.
Active Directory stores information about an organization’s resources in a central database, which can be accessed by authorized users and systems. It provides a range of features and tools to help administrators manage and secure access to these resources, including user authentication, user provisioning, access controls, and security policies.
Active Directory is typically implemented on a network of servers running the Active Directory Domain Services (AD DS) role. These servers, known as domain controllers, provide access to the Active Directory database and manage requests for access to resources. It is a key component of many IT infrastructure systems and is often integrated with other tools and technologies, such as Microsoft Exchange and SharePoint.
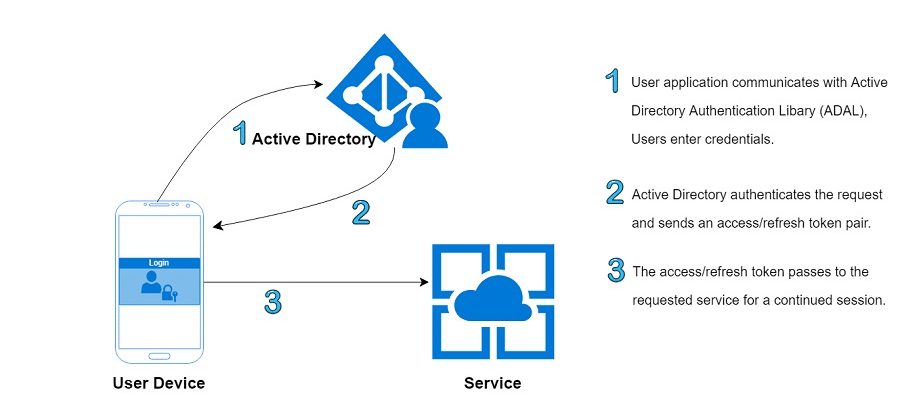
Below figure explains Active Directory authentication process.
Major attacks on Active Directory
Golden ticket attacks: This type of attack involves an attacker creating a forged Kerberos ticket that allows them to gain access to resources within an organization’s IT infrastructure.
Pass-the-hash attacks: In this type of attack, an attacker uses a stolen password hash to gain unauthorized access to a system.
Kerberos delegation abuse: This type of attack involves an attacker using Kerberos, a network authentication protocol, to gain access to resources that they are not authorized to access.
DCShadow attacks: This type of attack involves an attacker modifying Active Directory data to gain unauthorized access to resources or to manipulate data within the directory.
DCSync attacks: This type of attack involves an attacker using a domain controller’s replication functionality to extract sensitive data from an organization’s IT systems.
See more: Deloitte India & Palo Alto Networks enter into strategic alliance
Brute force attacks: This type of attack involves an attacker using automated tools to try a large number of different username and password combinations in an attempt to gain access to a system.
Privilege escalation attacks: This type of attack involves an attacker attempting to gain higher levels of access to a system or network by exploiting vulnerabilities or misconfigurations.
Below some steps one can take to protect Active Directory against attacks
Use strong passwords: Require users to use strong, unique passwords for their Active Directory accounts, and enforce regular password changes to prevent the use of compromised passwords.
Enable multifactor authentication: Use multifactor authentication to require users to provide additional proof of their identity when accessing Active Directory resources. This can help prevent unauthorized access even if a password is compromised.
Monitor and track access: Use tools such as security information and event management (SIEM) software to monitor and track access to Active Directory resources. This can help identify suspicious activity and allow you to take appropriate action.
Use access controls: Implement granular access controls to limit the resources that users can access within Active Directory. This can help prevent unauthorized access to sensitive data.
See more: Strelastealer malware targeting Outlook and Thunderbird users
Keep systems and software up to date: Regularly apply security updates and patches to Active Directory and other systems to help protect against known vulnerabilities.
Use security best practices: Follow best practices for securing Active Directory, such as using complex passwords, enforcing access controls, and monitoring and tracking access.
Train users: Educate users about cyber threats and how to identify and avoid them, such as recognizing phishing attacks or suspicious emails. This can help prevent user mistakes that could lead to attacks on Active Directory.
We hope you found article interesting. For more exclusive content follow us on Facebook, Twitter and LinkedIn






