
What is Petya ransomware – Latest Hacking Updates
What is Petya ransomware – Latest Hacking Updates Petya ransomware is a type of malware that caused significant damage to organizations around the world in

What is Petya ransomware – Latest Hacking Updates Petya ransomware is a type of malware that caused significant damage to organizations around the world in

What is Locky Ransomware – Latest Hacking Updates Locky ransomware is a type of malware that was first discovered in 2016. It is a form

Know about WannaCry ransomware – Latest Hacking Updates WannaCry ransomware is a type of malware that caused a global cybersecurity crisis in May 2017. The

Ransomware – its type and countermeasures against ransomware Ransomware is a type of malware that encrypts the victim’s files and demands payment, typically in cryptocurrency,
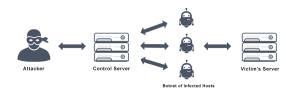
Distributed Denial of Service (DDoS )attack type and mitigation DDoS, or Distributed Denial of Service, is a type of cyberattack in which an attacker floods

Scammers dupe millions from companies through the “boss scam” Recently, the Delhi Police (India’s capital) commenced an inquiry into scammers who pretended to be Indigo

10 ways Artificial Intelligence can reshape Cyber Security in future Artificial intelligence (AI) is a broad field of computer science concerned with creating intelligent machines
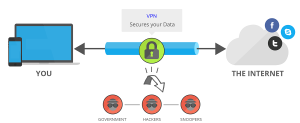
What is VPN – Difference between SSL VPN and IPSec VPN VPN stands for Virtual Private Network, and it is a technology used to secure

Kevin Mitnick – A most wanted hacker turned security consultant Kevin Mitnick is one of the most famous computer hackers of all time, who has
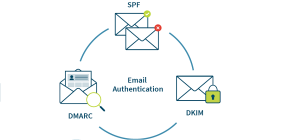
What is email authentication – SPF, DMARC and DKIM Email authentication is the process of verifying the identity of the sender of an Email and
© 2024 -Latest Hacking Updates | Site Designed and Developed by – Traffic Tail

Subscribe to our weekly newsletter below and never miss the latest News.